On October 27, 2016 three middle-aged men were gathered in a room in Hotel Cathedral in the center of Ghent. All three typing away on a laptop.
“Uh oh”, one of them said.
A Twitter login screen displayed the Twitter handle @realdonaldtrump alongside a few password dots. Twitter also asked for an email address verification. ‘[email protected]’ didn’t work, an error message appeared. And the login attempt failed. Remarkably, in a way that had not been foreseen. The email address was incorrect, the password however, matched!
“Did you use a VPN?”
“No. I didn’t think the password would work”.
Was this a cyber-attack on an American presidential candidate?
All three of them realized what this meant. The login attempt had been made using the hotel’s Wi-Fi. The Twitter log files now showed that there had been an attempt to log in on the account, from their hotel, using Donald Trump’s legitimate password. And these logfiles would undoubtedly be transferred to the U.S. intelligence services.
It could be perceived as a cyber-attack on an American presidential candidate.
Something that could get them into trouble and ruin their reputation, something they could not afford to let happen.
Grumpy old hackers
I first met with Edwin, Mattijs and Victor in June, in Amsterdam-Noord. “Up the stairs, first door on the left”. I enter a James-Bond-like setting, a room with high windows and a view of the IJ river, a dock with a drilling tower and a Russian polar ship. The three men are sitting at a large conference table. On the table, a few bottles of Club-Mate, the hacker’s preferred beverage.
It is immediately noticeable that the three of them are close. They have some resemblance to members of a rock band. Victor the talkative guitarist, Mattijs the thoughtful bass player and Edwin the grumpy drummer, who occasionally intervenes when the conversation tends to stray. All three are members of the GGOH – The Guild of Grumpy Old Hackers. Their website displays an image with eight pirates and a bitcoin address. “No one has ever transferred a single bitcoin to us, though”.
The GGOH has about ten members: ‘Elite’ older hackers. Everyone has their own specialism. They do things the police or the army won’t or can’t do. They carry information they can’t ever share. They have decent day time jobs. Large corporates hire Edwin and Mattijs to help them with their information security. Victor is employed by a government agency. At night, however – they run ‘projects’. They love algorithms and the law, because where there are rules, mistakes happen. “Loopholes. Forgotten things.” says Edwin, “Such as the fact that churches have access to the municipal personal records database. Somewhat weird. The kind of thing that will trigger us to start a church of our own.”
“Yes, the three of us could immobilize the country. And so could you. By yourself.”
They aim to locate these mistakes before criminals, spies and terrorists do. And while doing so, they come across the craziest things. Such as bridges that can be opened via the internet, telescopic traffic bollards that can rise from the pavement using a laptop and pension funds that can be accessed with very limited difficulty. They are very careful to not mention specific examples. Mainly because of signed confidentiality agreements with clients. But also to not give others any ideas. “Yes, the three of us can immobilize the country”, says Mattijs, “but so can you, by yourself”.
In order to securely exchange information with colleagues working in information security, they attend hacker conferences such as BlackHat and DEF CON in Las Vegas, BruCON in Ghent and the Chaos Communication Congress in Leipzig, where I first heard about their story. “Dutch hackers hacked Trump’s Twitter account just before the 2016 elections”, someone there said.
Within a small bubble of the hacker community it was known who they were. And after a few months of strong persistence, the grumpy hackers agreed to speak with me. I was allowed to write up this story, on the sole condition that I would only mention their first names.
Digital treasure trove
In October 2016, the grumpy hackers attended another hacker conference. One they never miss: BruCON, held in the Aula Academica in Ghent, a nineteenth-century neoclassical building with Corinthian columns and a small lecture hall in the shape of an arena.
“We normally sit center downstairs, a little towards the back”, says Victor, “We do that mostly for me. I don’t like any hustle and bustle around me, and I also like to keep a little oversight. We listen to the talks and dig around on our machines a little bit in the meantime. But this time we were on the second floor, very high up. On very unpleasant wooden benches. And then there was a talk from someone I personally like very much, but the presentation contained incredibly annoying sheep sounds. Really. Every single slide: mèèh. So then Edwin said, ‘Yo that stolen LinkedIn data file has now been made publicly available’. That’s pretty cool, let’s go check it out”.
And so, accompanied by sheep chatter, the grumpy old hackers left the auditorium to go take a look at the LinkedIn file.
Everyone in information security had heard about ‘that LinkedIn database’. A digital treasure trove with 120 million usernames and hashes of passwords (see insert below to this piece). The loot of a digital burglary in 2012. The mastermind was Yevgeni Nikulin. Google his name and you will find his picture near a Lamborghini parked in front of the Basilius Cathedral on the Red Square in Moscow.
According to the lawsuit documentation now pending against him in the United States, he managed to get LinkedIn employees to click a link in an email and infected their computers with malware. Through these computers Nikulin managed to gain access to the internal LinkedIn network.
Dark market
Nikulin made a ton of money selling information to people in a secret criminal network. It is no coincidence that shortly after the LinkedIn break-in, Donald Trump’s Twitter account was hacked. On 21 February 2013, song lyrics by rapper Lil’ Wayne appeared on Trump’s Twitter account. Trump, who had ‘only’ two million followers at the time, reacted immediately:
‘My Twitter has been seriously hacked – and we are looking for the perpetrators’.
It wasn’t until the summer of 2016 that the LinkedIn file popped up on the black market. For 5 bitcoins – at that time the equivalent of about three thousand euros – it was offered on The RealDeal, a well-known dark market. This seemed very appealing to the grumpy old hackers.
“When you are responsible for the information security of a large company or a government agency, you will want access to such a database to see if it contains data of people from your own organization. Three thousand euros isn’t much for a database like this. If you only knew how many intelligence services would be willing to pay for this”, says Victor. “However, buying stolen data is a criminal offense. It is illegal, and we wouldn’t ever consider doing that. We’re not keen on financially aiding criminals. Also, the police access the dark markets too. They can identify buyers. It was absolutely out of the question for us to acquire that file”.
Mark Rutte was on that list. So was Mark Zuckerberg.
Security researchers who infiltrated criminal networks got their hands on the database, regardless. Within the information security community, these types of files are shared in order to better test one’s own security. Something that is impossible to do out in the open.
Edwin was the first to receive a link, which he immediately shared with Mattijs and Victor. They quickly left for the hotel to quietly conduct further research.
“I instantly found my director’s password in there”, says Victor, “I sent him a brief message, saying ‘look, it’s your password”. Dutch Prime Minister Mark Rutte was on the list. And so was Mark Zuckerberg (‘dadada’ – turned out afterwards that the password for his facebook account was ‘tadada’).
‘Ethical hackers’
A week and a half prior to the US elections, everyone in the information security domain was talking about Trump’s Twitter account. It was the most wanted target in the world. From hacktivists to foreign intelligence agencies, they were all out for that account. It was therefore very instinctive to check if Donald Trump was also in the database.
And he was, right there.
email: [email protected]
password hash: 07b8938319c267dcdb501665220204bbde87bf1d
Using the program John the Ripper – a tool hackers use to crack hashes – Mattijs identified the password in less than a second: yourefired
Edwin was typing it in before anyone could say anything.
The password was accepted, and as an extra verification step an email address had to be entered.
But the entered address was incorrect.
Edwin almost fell off his chair. It meant that Trump hadn’t changed his password after the 2013 ‘hack’.
Which was bad news.
There was no time to waste. If anyone else would now hack Donald Trump’s Twitter account, they were the ones to be potentially blamed.
The grumpy old hackers knew better than anyone that the Twitter administrators would be able to see that they had made a login attempt from their hotel with the correct Donald Trump password. And also that this information would sooner or later be passed on to the U.S. intelligence services. A login attempt on Donald Trump’s Twitter account could be perceived as a cyber-attack on a U.S. presidential candidate.
So there really was only one option. The grumpy hackers would have to prove that they were real ‘ethical hackers’. In order to demonstrate this in an unambiguous way, however – they would have to, ironically, break into Trump’s account. It would be the only way to prove that they had actually accessed the account – without doing anything else.
They had no time to waste. If someone would now hack Donald Trump’s Twitter account, they would be the ones to be potentially blamed. They searched the internet and databases for all the email addresses Trump used. After about an hour, they found it.
[email protected]
The password matched.
And so did the email address.
But again, they failed to break into the account. Access was still being denied because the Twitter algorithms detected that the login attempt had taken place from an illogical location: Europe. Which was physically too far away from the location where Trump had last logged in: New York.
The Grumpy Old Hackers knew how to bypass this, however. They located an open proxy server in New York. A computer that can be used as an intermediate station to mask where a signal is originally coming from.
Enter.
And…
They were in Donald Trump’s Twitter account. Holy fuck!
“I said ‘W00t!’” says Victor. W00t is the international hacker’s exclamation of success and excitement.
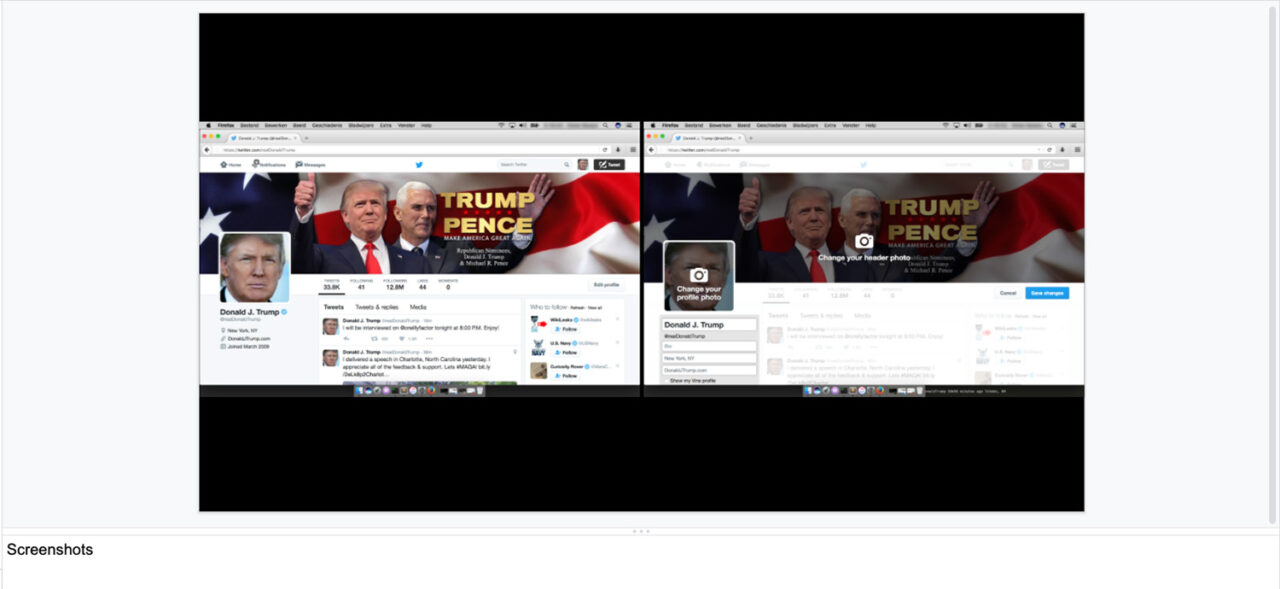
They could now change Trump’s Twitter banner and his photo. Read his DMs. And they could tweet – whatever they wanted – in his name.
This was the most wanted hacker target of the moment! It wasn’t the launch codes of the nuclear missiles, but you could come pretty close, cracking a creative grumpy hacker brain over this. One tweet from Trump could cause the stock market to plummet. A tweet from this account could endanger world peace.
So, what now, then?
What could they do next?
They certainly knew what they had to do. They would now have to document each and every step of the process. Take screenshots. Draft a detailed report, just as they would do when they would detect a leak at a company or a government agency. They could then hand over this report to Homeland Security as proof that they had broken in, and yet had ‘done nothing else’.
But what were the limits of their power?
They were holding a weapon that could prevent Trump from becoming president. (Something that didn’t seem very likely at the time, by the way).
Datadump
They sat in a Belgian cafe all night to discuss. They realized that Trump mighthave never changed his password but had always changed his e-mail address. And that he used the same password everywhere.
They calculated the different encryptions that could be made of a combination of passwords (see insert below – some hashes are hard to crack.) And they checked if they encountered these codes in other databases.
And they did. Trump never changed his password. He only changed his e-mail address.
[email protected]
d*******@gmail.com
[email protected]
[email protected]
His password also popped up in other leaked databases, such as those of Newerth, Evony and Minecraft.
Meaning he played computer games on his Android phone. “But the most remarkable one we found”, says Victor, “was Ashley Madison”.
Ashley Madison is a Canadian dating platform for married people. In 2015, criminals stole all its user data: names, addresses, credit card details, and sexual fantasies.
Within a few hours the grumpy old hackers had gathered a wealth of information that could potentially make others very happy.
Victor (apologetic): “This data dump is considered the most unethical hack of all time. It has caused damage to many people’s private lives. In some countries people jumped off buildings to put an end to it all. Using this type of data is something you would only very carefully consider. In any case, we checked if Trump was in the database. He was”.
Not only his login details, but also his credit card details.
Within a few hours, the grumpy old hackers had collected a wealth of information that could potentially make others very happy: the Chinese, the Russians, hacktivists, the Democrats.
What if they changed the password? Would they be able to sell it? What could they sell the information for? Should they tip off a hacktivist? Should they upload a new background? What if they tweeted something? And if they tweeted something, what would it be? A joke? It would provide great opportunities for self-promotion.
“’I quit, vote Hillary’. Thought that was the best one”, says Edwin.
Pissing off Trump
At the same time, they realized that if they had been able to find all of this so quickly, others would be able to do the same. Scenarios in which other hackers, criminals, or intelligence services would do something and then blame them started becoming increasingly imaginable.
They drafted a detailed press release containing all the screenshots and logs so that they could issue these in case of a severe escalation. A document that they could pass on to a governmental department, or to journalists, to prove that they had ‘acted ethically’.
Then, they sent an e-mail to Trump. They cc-ed the USCERT (The United States Computer Emergency Readiness Team of the Department of Homeland Security). The message stated that they were in possession of Trump’s login details and suggested him to change the password to something along the lines of ‘MakeAmericaGreatAgain2016’.
But no response came.
Subsequently, they contacted the NCSC, the Dutch CERT.
Via the NCSC, they were informed that ‘the message had arrived’.
People keeping a close eye on the media at the time could tell that ‘something’ had transpired. The New York Times reported that ‘assistants’ of Trump were suddenly in charge of managing his Twitter account. Obama addressed this, during a speech held in Florida: “Now, if somebody can’t handle a Twitter account, they sure can’t handle the nuclear codes”. It was clear that the email had been received and that it had resulted in Trump no longer being allowed to tweet. It was also clear that Trump wasn’t happy about that.
And when you piss Trump off, you have a problem.
Trump’s fuel seems to be revenge
‘Revenge is sweet and not fattening.’
Trump once tweeted this quote from Hitchcock in full confidence. Revenge is Trump’s middle name. It seems to be what fuels him. A considerable amount of his time is spent on retaliation. In 2011 he addressed the National Achievers Congress in Sydney to explain the secret of his success. “Get even with people”, he said, “When they screw you, screw them back – ten times over. I truly believe in that”.
In 2012 he said, “When someone hits you, hit them back five times harder than they ever thought possible. You have to get back at them. Get even. And the reason why you need to do this is very important… When they do something like that to you, you need to immediately show you are not to be messed with and that no one is to take advantage of you. It’s not even personal, although it does make you feel good – to be honest. I’ve done it many times. Others will witness this and say, ‘Let’s leave Trump alone’, or ‘Let this one go. They fight too hard’.”
“We hoped for some reassurance, but they never provided any”…“If this explodes”, they said, “there won’t be much we can do for you”. “Ha ha.”
“He also has followers who are extremely fanatical”, says Victor.
“It was quite an exciting period”, says Edwin.
They have a good laugh about how Mattijs got scared when a helicopter flew over during a phone conversation.
“I live in the embassy area”, Victor says, “They would be with me within minutes”.
The grumpy hackers contacted acquaintances within Dutch governmental services. What if something were to happen? What were their thoughts on the risks?
“We hoped for some reassurance”, says Edwin, “But they never provided any”…“If this explodes, there’s not much we can do for you”, they said. “Ha ha.”
All good!
A few months went by, and nothing happened. In the summer of 2017, the guys wanted to attend DEF CON, in Las Vegas – the largest hacker conference in the world – and much like BruCON – an annual happening.
“I was denied an ESTA (visa waiver) to enter the US”, says Mattijs, “Which was a bit cathartic”.
In the end it was resolved and they each flew to Las Vegas independently.
“Someone gave me a number to call just in case”, says Edwin. “There are some associations whose existence is unknown to most. Entities that extract people and bring them back home when they have been taken hostage in Namibia or something like that. They knew about the situation and where we were going to be”.
Edwin had also left an encrypted flash drive containing passwords at home. “Those passwords would provide access to the report we had drafted. If we would get arrested in the US, then the drive could be accessed. You know – ‘this is what happened, and this is what we did’. Just in case someone like Trump would really be out to get you. It would help us get ‘properly’ arrested and put away neatly, just in case. Because for all I care, they could also just shove me in orange overalls, and you would never hear from me again. All these things kept circling my mind”.
Mattijs was the first to sail through. When he got through customs, he rang the others: “It worked!”
“Ha ha ha. At the time, we didn’t realize that getting in wasn’t the problem”, says Victor.
Utterly nerve wrecking times
DEF CON 2017 was Marcus Hutchins’ show, ‘the man who had saved the internet’. In May 2017 the Wannacry virus spread from computer to computer. Within a few days, the ransomware had infected an estimated 200,000 computers in 115 countries. And there seemed to be no end in sight. British hacker Marcus Hutchins studied the source code of the virus and found a reference to a mysterious web address. A web domain that was still free. He then decided to reserve the domain of the website, to see if something would be written to it by the virus. Much to his surprise, the ransomware attacks bluntly stopped from one moment to the next. Hutchins had accidentally found the kill switch. A real hero. And he wanted everyone to know. At DEF CON 2017, he partied continuously at his Las Vegas Airbnb mansion and swimming pool.
For years the men kept things quiet. They never even told their girlfriends.
In the early morning of August 3, 2017, he was ready to leave for England, albeit slightly hungover. Just before boarding, two men pulled him from the line, handcuffed him and escorted him away.
Hutchins turned out to have a criminal youth record and was apprehended. The news of his arrest spread rapidly within the community.
“That was in the morning of my departure date”, says Mattijs, “I was scheduled to fly back home in the afternoon and was freaking out”.
Those were perhaps the most nerve wrecking moments. To their great relief, Edwin, Mattijs and Victor were able to leave the country again. For years the men kept things quiet. They never even told their girlfriends.
The reasoning behind coming clean now, is that the case provides for a good example of responsible disclosure. “Whatever you may think of Trump as a person, we did the right thing”.
Setting the example
Victor, Edwin and Mattijs are ethical hackers. Comparable to a digital voluntary fire brigade. When they detect smoke, they flag and make sure that fires are contained. Whether it concerns Mother Theresa’s house, or Donald Trump’s. It doesn’t matter. In addition, they contribute to the Dutch police’s Hack Right project, aimed at young hackers between the ages of 12 and 23. The project’s goal is to get ‘first offenders’ back on the right track. They’re much like old boxers trying to teach young fighters manners.
“Since we are a bit older, it is easier for us to get through to young cyber criminals who have crossed the line”. What also helps, is that the grumpy old hackers weren’t real saints when they were younger either, engaging in digital mischief at times. “Back then we were very lucky not everything would get registered, and we can be very grateful for that”, says Mattijs. “We managed to get away with things. But we’ve been pretty naughty at times. The big advantage to this is that we truly understand what young people are struggling with right now”.
“We will make sure that someone who gets caught for the first time, is not immediately sent to prison, but gets onboarded on a project with us instead”, says Edwin, “In order for him or her to learn what hacking really is about, with proper guidance and coaching, and to avoid a relapse. This is an official program. We have quite a few connections within the Public Prosecutor’s Office and the police”.
“Let’s put it this way: In hindsight, with everything we know now, we might have made different choices.”
In brief, the grumpy old hackers are setting the example. And having to do things the right way with someone they ‘may not like very much’ really proves how responsible disclosure works. The process of unsolicited reporting of a security risk.
But what if Trump’s DM’s would have contained indications of ties with right-wing extremist groups? Wouldn’t it have been a responsible thing to report that?
“Let’s put it this way: perhaps in hindsight, with everything we know now, we would have made different choices”, says Victor. “In any case, I’m glad we were the ones to find the leak, not someone who is much less experienced. Things would have probably gone horribly wrong. When you get that far, at such a specific moment in time, and with that specific political backdrop… Have you seen the movie Hackers?
In that 1995 cult film a group of people hacks national US broadcasting, which is witnessed by everyone. By people carelessly watching TV, people looking at the window showcases of retailers in electronics, the media bosses in their big offices. A hacker with dreadlocks addresses the nation as if he were the head of state. ‘I kinda feel like god’, he says.
Well, that feeling never goes away – even after 25 years. You’re somewhere you’re not supposed to be. Which is pretty unique. You’re somewhere where not many people can say they’ve been. It is a feeling you need to learn to manage and control”.
This publication was made possible with the support of Fonds Bijzondere Journalistieke Projecten.
Hashes
Hashes are specially encrypted passwords. They are so-called ‘one-way functions’. It is easy to calculate a hash of a word, yet impossible to do the opposite.
It is comparable to a fingerprint. If you have a fingerprint of someone, it is impossible to reason back which person it belongs to. Fingerprints are only worth something if you have large databases with a lot of fingerprints linked to people.
That’s why databases with a lot of password-hashes are worth their weight in gold. You can calculate the hashes of common passwords and see if these hashes are in the database. Just Google ‘sha1 hash generator’ and you will be able to easily verify that if you run the password ‘12345’ through the hash mill, the result is the next hash:
8CB2237D0679CA88DB6464EAC60DA96345513964
If you have a database with usernames and SHA1-hashes, you can then search for the code here above, to find out which users have the password ‘12345’.
You can also calculate the hashes of all words in a digital dictionary. This is one of the reasons why it is a bad idea to have a password from a dictionary. It is also the reason why it is good to alternate between uppercase and lowercase characters. The hashes also change when you replace a lowercase with an uppercase character.
Partly due to Victor’s persistent interactions with Twitter, it is now mandatory to have two factor authentication on a verified account, so that you are not only required to log in, but are also required to type in a code that will be sent to you via your phone, for example. This makes hacking an account much more difficult.
It was a big surprise when on 15 July 2020 suddenly strange tweets appeared on the timelines of Barack Obama, Elon Musk, Bill Gates and Jeff Bezos. They promised to transfer bitcoins (if you first transferred bitcoins to them). A number of people fell for it. In the meantime, 17-year-old Graham Ivan Clark was arrested. It seems that through social engineering (calling and deceiving Twitter employees) he somehow gained access to the Twitter backend.
Striking detail: Donald Trump’s Twitter account was left alone this time. It seems his account has extra protection these days.



Je reactie wordt geplaatst zodra deze is goedgekeurd. Je reactie is geplaatst.